Has anyone in Europe bought a Vision Pro from another European country, with optical inserts? Do foreign prescriptions work? Asking for a friend, obviously, I would never…
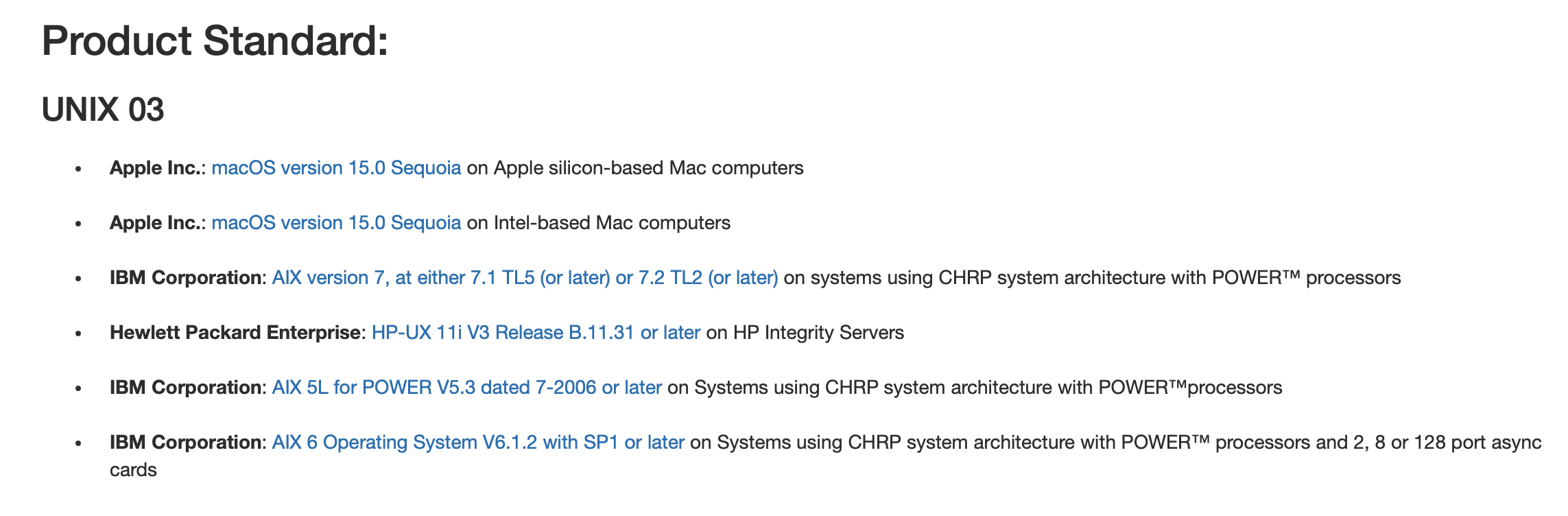
Apple, IBM & HP appear to be the only remaining active UNIX vendors: www.opengroup.org/openbrand…
(The fun part was that it was new snow, temperature hovering around 0-1 °C so it was basically a few centimetres of slush to bike through.)
(But at least it wasn’t raining!)