I really want to stay up to watch the Ax-3 launch but I also really need sleep. I am exhausted from looking at C++ all day.
Throwback to January 2010 when we found The Internet at the office. Turns out it was guarded by tiny F-Secure penguins.

It was pretty nice to see this sunset on my commute from work a couple of days ago. Apologies for the bad camera work, it is hard to shoot video from your phone while biking, especially with glove an and when there’s ice and snow on the ground. 🙂
Saw this and started wondering what kind of pub an astropub would be
(also, I miss the pineapple burger they used to serve there!)

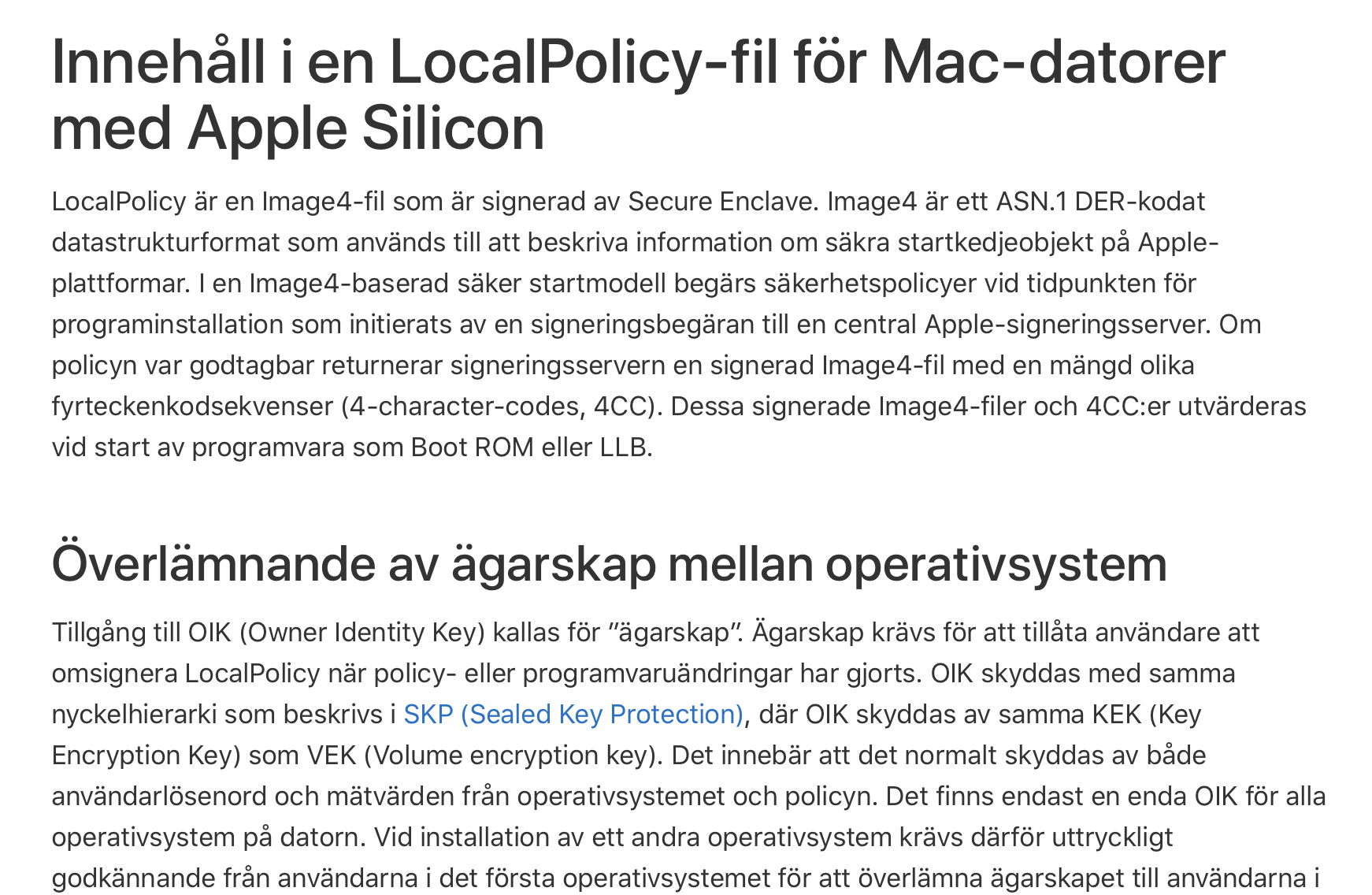
Apple localizing deeply technical content is nice, but reading it in Swedish makes it hard to follow, because the terminology is so unfamiliar. I actually can’t get the English version for cross-checking because it redirects me to the Swedish version even if I manually enter “en-us” in the URL.